GKE Workload Identity
This document shows you how to configure Workload Identity on Zeet Project. Workload Identity allows app deployed in GCP to use IAM service accounts to access Google Cloud services.
Step 1. Create a service account in GCP with the desired permissions
You can create a account using CLI commands below or any preferred method.
gcloud iam service-accounts create GSA_NAME \
--project=PROJECT_ID
gcloud projects add-iam-policy-binding PROJECT_ID \
--member "serviceAccount:GSA_NAME@PROJECT_ID.iam.gserviceaccount.com" \
--role "ROLE_NAME"
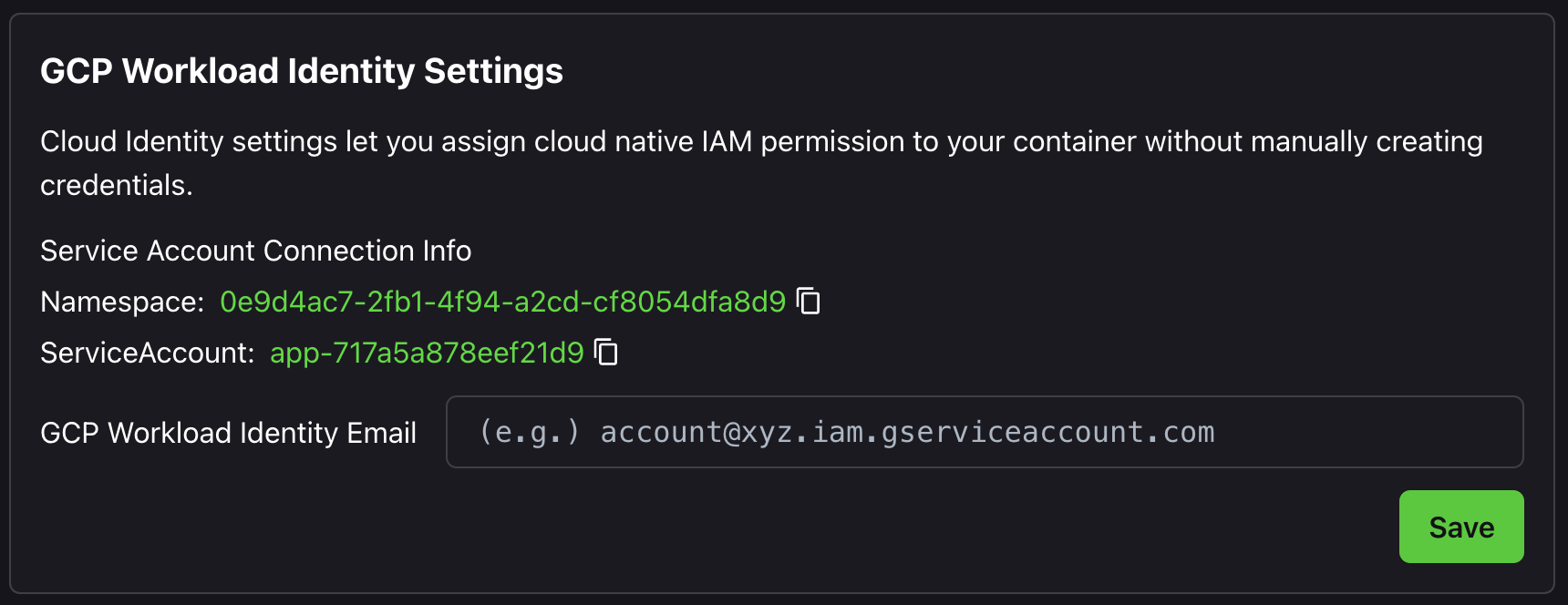
Step 2. Find the Zeet Workload Identity info
The advanced settings page on Zeet will show the Kubernetes service account namespace and name.
Step 3. Grant Zeet Project the permission to use the GCP Service Account
Now we use the information above and add roles/iam.workloadIdentityUser to the previously mentioned GCP service account.
gcloud iam service-accounts add-iam-policy-binding \
GSA_NAME@PROJECT_ID.iam.gserviceaccount.com \
--role roles/iam.workloadIdentityUser \
--member "serviceAccount:PROJECT_ID.svc.id.goog[NAMESPACE/SERVICE_ACCOUNT]"
Example: For GCP Project Id zeet-demo and namespace 8da2d9e2-06a6-46f2-9668-75d539e37fa1 and service account name app-12345, the correct member name for policy binding will be
serviceAccount:zeet-demo.svc.id.goog[8da2d9e2-06a6-46f2-9668-75d539e37fa1/app-12345]
Step 4. Add the GCP Service Account info to Zeet
Simply add the account id GSA_NAME@PROJECT_ID.iam.gserviceaccount.com to the input and save.
Now your Zeet app will be automatically authenticated with the GCP service account.