Private EKS Cluster Connection via PrivateLink
This guide provides step-by-step instructions for establishing a private connection to an Amazon EKS cluster using PrivateLink, specifically tailored for Zeet. PrivateLink allows secure communication between your Amazon VPC and EKS cluster without exposing your cluster to the public internet.
This guide demonstrates the process through the AWS Management Console. However, if desired, the steps can be converted into Infrastructure as Code (IAC) workflows.
This guide will refer to AWS Docs on sharing your services using PrivateLink. The AWS Docs go in deep detail about the background and process of sharing your services. This guide points out the necessary steps and information required to set this up with Zeet.
1. Create a PrivateLink Endpoint for your EKS Control Plane
Follow the instructions provided in the official Amazon EKS documentation for creating a PrivateLink Endpoint for your EKS control plane.
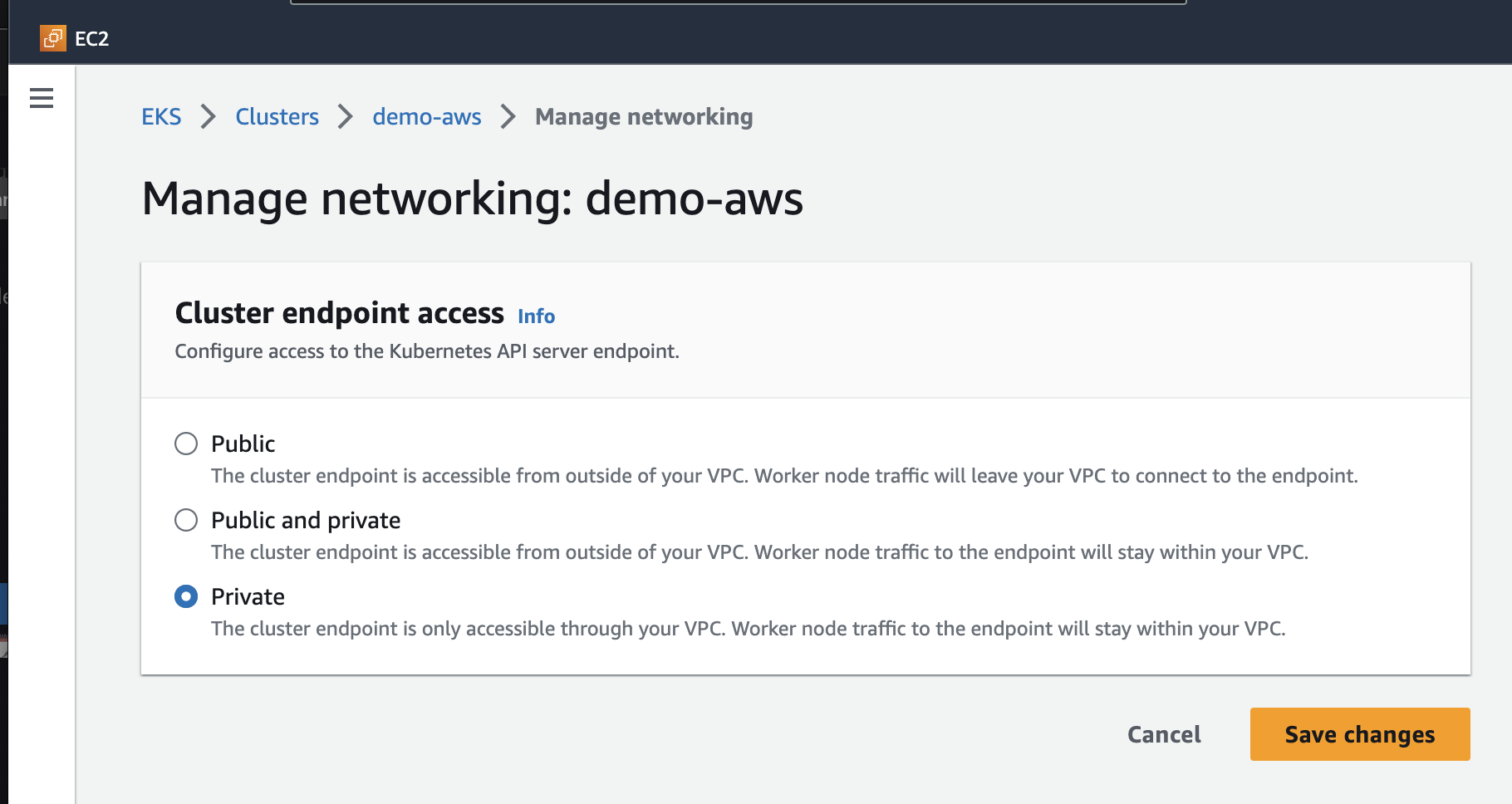
Ensure that the EKS endpoint has private endpoint access by navigating to the EKS cluster dashboard. Click on "Manage Networking" and then "Manage Cluster Endpoint Access."
2. Create an internal target group
Step 1. Specify Group Details
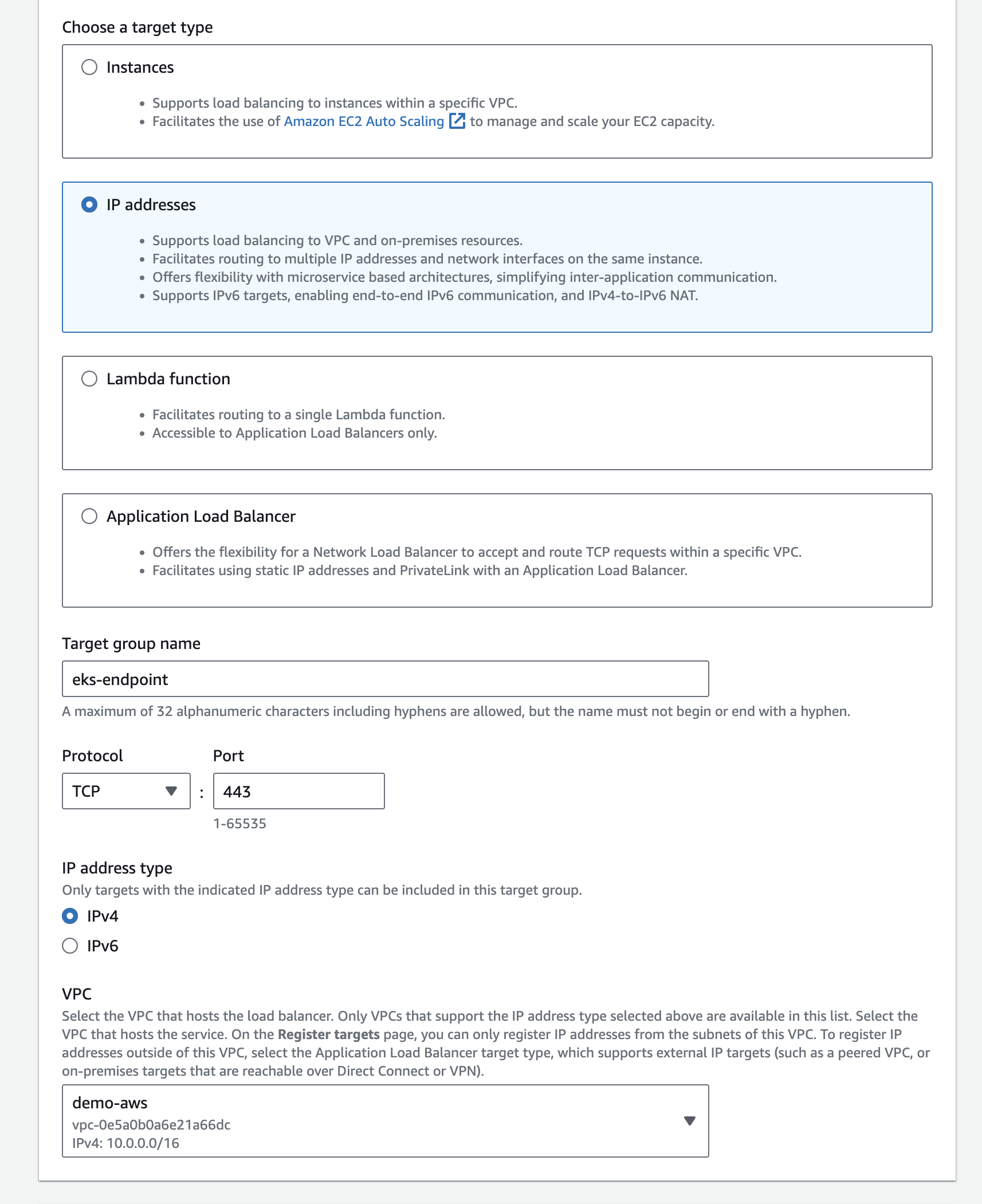
Visit the Amazon EC2 Console to create an internal target group.
- Set target type to be IP addresses
- Give your target group a name
- Set Port to 443 over TCP
- Select the VPC which contains your EKS Cluster
You can just use the default values for the rest of the fields.
Step 2. Register Targets
The second steps requires you to register your targets to ensure that your Load Balancer actually routes traffic to this target group.
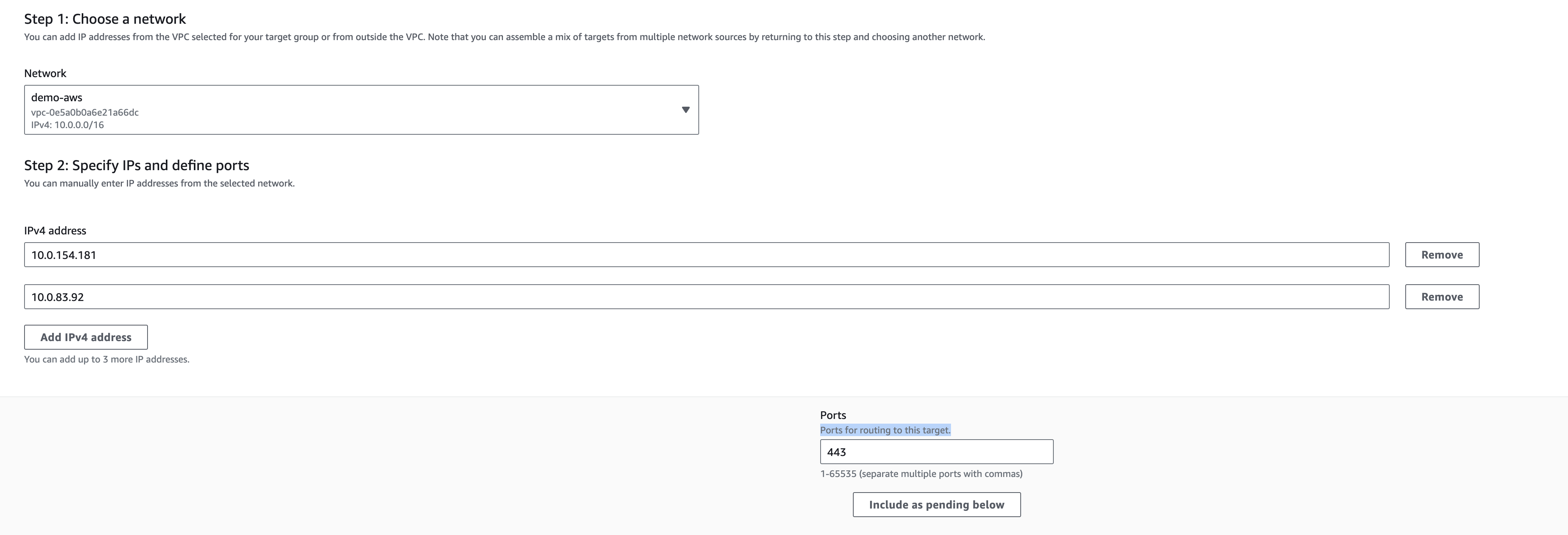
To actually get the IP addresses for your EKS Endpoint, you can run the dig command against your EKS endpoint address, which you can find in the "Overview" tab of your EKS Dashboard.
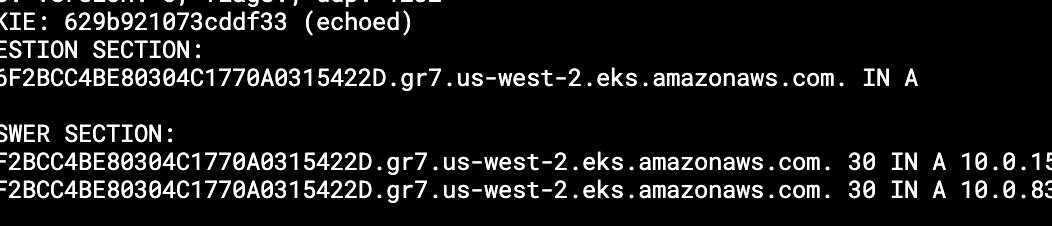
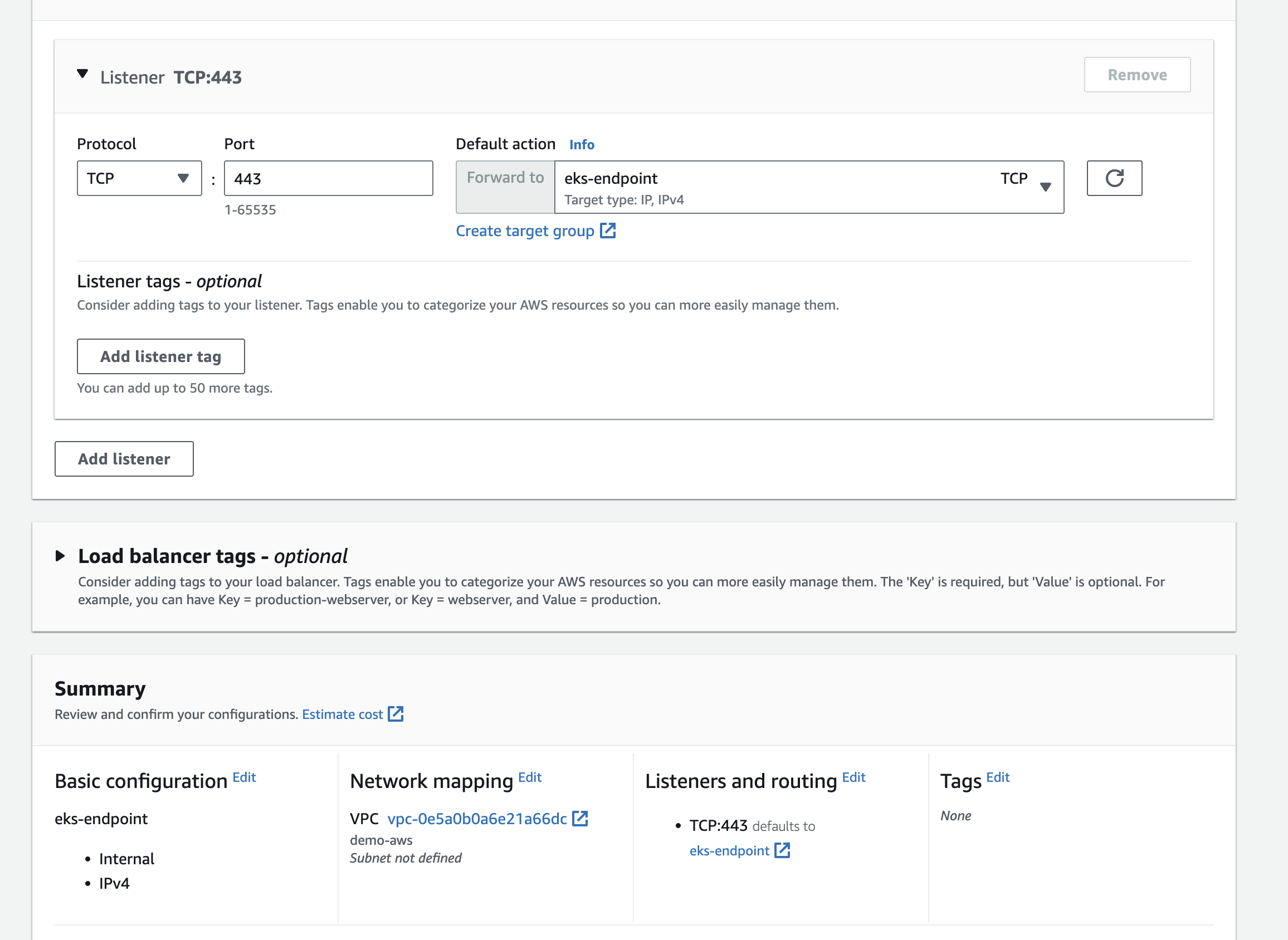
3. Create Load Balancer
Navigate to the EC2 Dashboard, into Load Balancers and create a Network Load Balancer. This Load Balancer must be in the same VPC as your EKS Cluster, and set the default action to forward to the target group you just created.
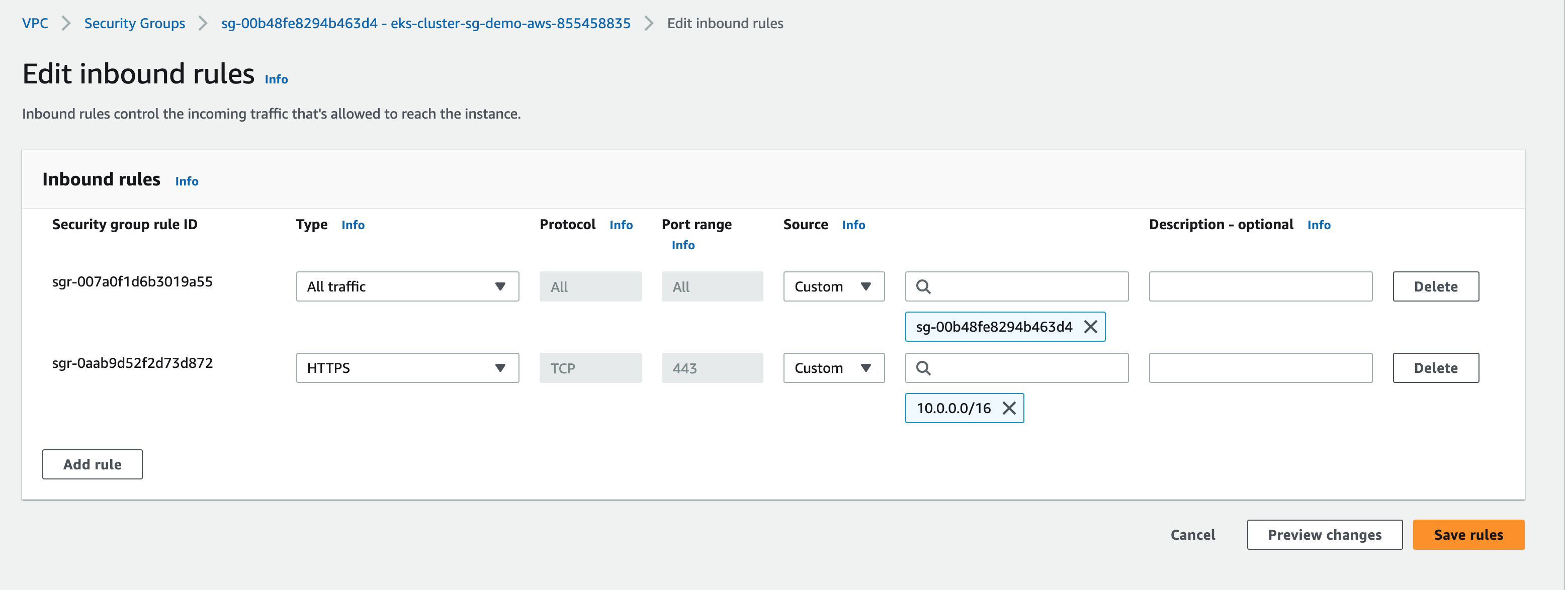
4. Allow inbound access to EKS endpoint
Now, we need to allow inbound access from the Load Balancer to the EKS endpoint. Navigate to Security Groups in the VPC Dashboard, and find the security group for your cluster. Here, click into "Edit Inbound Rules" and add a new rule with:
- Type - Custom TCP
- Protocol - TCP
- Port range - 443
- Source - Custom
The IP range 10.0.0.0/16 encompasses the entire VPC. For greater precision, you have the option to refine this by querying the internal IP addresses of the load balancers
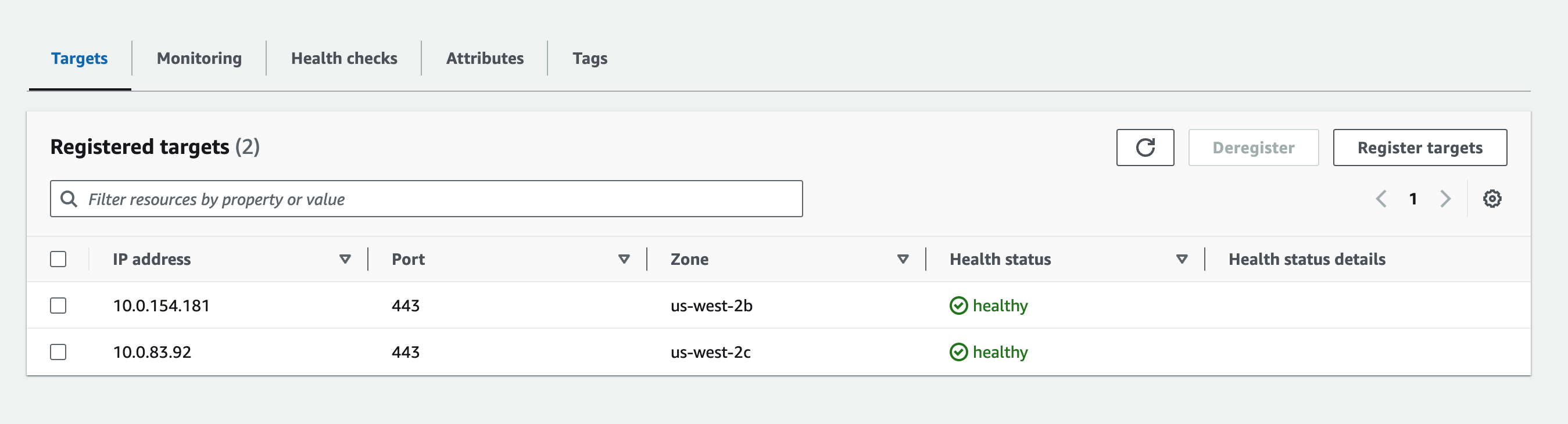
5. Verify Healthy Targets
Navigate back to the Target Groups page in the EC2 Dashboard. Click into the new target group you created, and verify that the Registered Targets are healthy.
6. Create VPC Endpoint Service
Access the VPC Endpoint Services page to create a VPC endpoint service with your Load Balancer.
Fore more information, read the Create an endpoint service section in the AWS Docs.
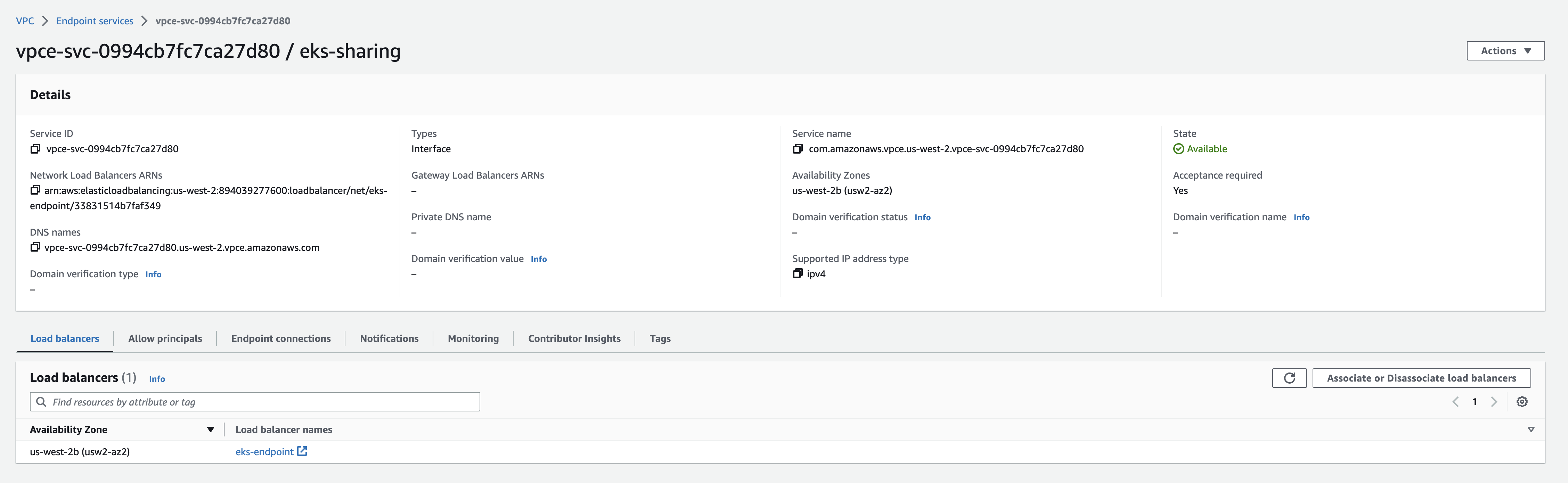
7. Share Endpoint with Zeet
For more information, read the Configure an endpoint service section of the AWS Docs.
1. Configure endpoint service permission
By default, your endpoint service is not available to service consumers. You must add permissions that allow specific AWS principals to create an interface VPC endpoint to connect to your endpoint service. You can use this ARN to authorize Zeet's production AWS account.
arn:aws:iam::349056421333:root
2. Provide Zeet with connection info
Service Name: com.amazonaws.vpce.us-west-2.vpce-svc-0994cb7fc7ca27d80 (example)
EKS Endpoint: YOUREKSCLUSTERID.gr7.us-west-2.eks.amazonaws.com (example)
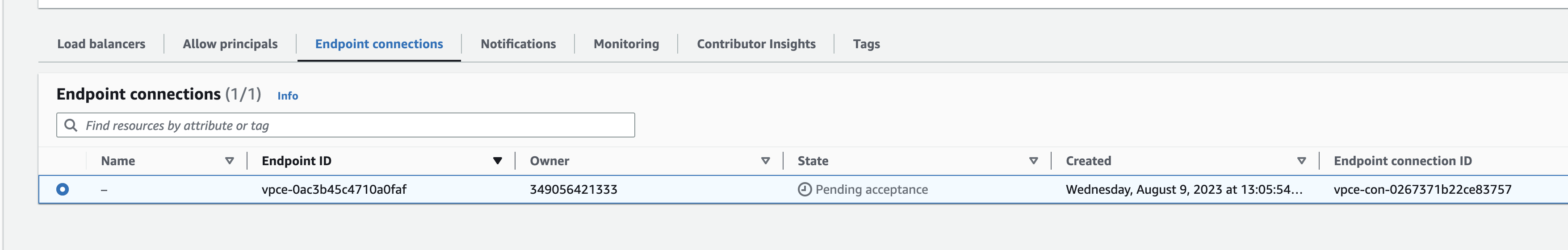
3. Accept endpoint connection request
After sharing your endpoint, you will get a connection/ access request which you will have to accept by clicking the Action button (not shown in screenshot). Refer to the Accept or reject connection requests section of the AWS Docs.